-
-
Mail Us

Basics of Cyber Threats

Network & System Security

Data Protection Techniques

Ethical Hacking Fundamentals

Cybersecurity is the practice of protecting computer systems, networks, and data from digital attacks, damage, or unauthorized access. It involves a combination of technologies, processes, and best practices to safeguard digital assets from threats like malware, phishing, and ransomware. The main goals are to ensure the confidentiality, integrity, and availability of information, and it requires a multi-layered approach involving people, processes, and technology

Core technical subjects
Network Security: Protecting networks from unauthorized access and other threats.
Cryptography: Securing communication and data through the use of encryption.
Ethical Hacking / Penetration Testing: Identifying vulnerabilities in systems by simulating attacks.
Application Security: Securing software applications throughout their lifecycle.
Digital Forensics: Investigating and analyzing digital evidence.
Cloud Security: Securing cloud-based resources and services.
Management and policy subjects
Risk Management: Assessing and mitigating security risks.
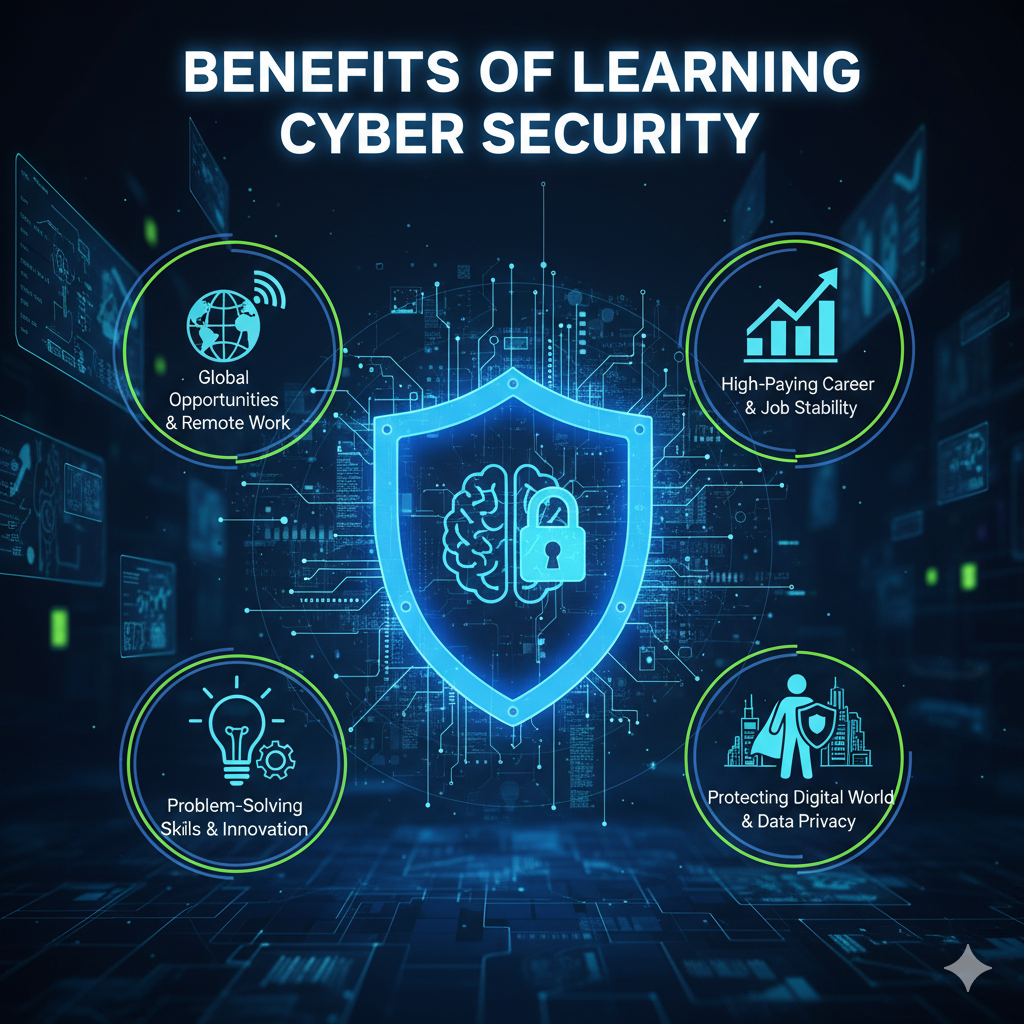
Protection from threats:
You learn to identify and defend against cyber threats like phishing, malware, and ransomware, protecting both personal and organizational data.
Enhanced problem-solving:
Cybersecurity training builds strategic and analytical thinking skills to tackle complex challenges, which are transferable to other domains.
Building trust:
For businesses, a strong cybersecurity posture builds customer confidence and protects the organization's reputation.

Experienced and qualified instructors Practical, hands-on training sessions Updated syllabus as per industry standards Certificate recognized for job opportunities